Think your password is secure enough?
- Use the controls in the Number Format area to specify the number format. In the Number Style For This Level drop-down list, select the number format you want to use. For example: '1, 2, 3,' 'i, ii, iii,' 'A, B, C.' To include the number from the previous level (or a higher level), choose the level from the Include Level Number From drop-down.
- Random Numbers Combination Generator Number Generator 1-10 Number Generator 1-100 Number Generator 4-digit Number Generator 6-digit Number List Randomizer Popular Random Number Generators. Games Lotto Number Generator Lottery Numbers - Quick Picks Lottery Number Scrambler UK49 Lucky Pick Odds of Winning Flip a Coin Roll a Die Roll a D20.
Adding 4 digit variable number to Name wordlist. Mohsen95 Junior Member. Posts: 1 Threads: 1 Joined: Nov 2017 #1.
You may want to think again. In 2014, nearly half of Americans had their personal info exposed by hackers – and that doesn’t even count the many companies that experienced breaches.
And with more and more businesses storing their information in the cloud and using SaaS solutions like business intelligence and hr software platforms, keeping your information safe becomes even more important.
Selecting an obscure and complex password and changing it frequently can spell the difference between keeping your data secure and having your personal information stolen. We’ve gathered insights and advice to empower you to tighten up your online security – and keep hackers out of your personal business.
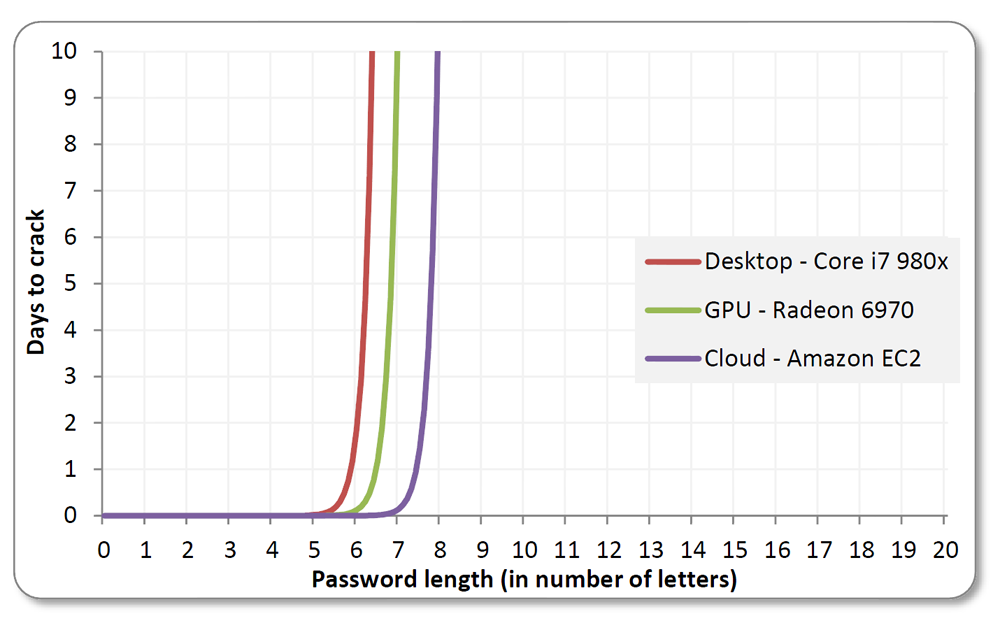
To get started, we set out to discover just how quickly a seasoned cracker could “brute-force” various types of passwords (systematically check combinations until finding the correct one) based on factors such as length and character types. We also created an interactive feature that lets you estimate how long it would take someone to crack a password now compared with how long it took in the past. If you come up with an idea for a potential password, our tester can tell you just how secure it is. Just how many days, weeks, or years worth of security an extra letter or symbol make? How does password strength change over time? The answers just might surprise you.
How strong is a typical password now – and how strong was it in the 1980s? Enter a word (not your current password) and drag the slider to select a year to find out how long it would take for someone to crack the term if it were your password. It could take anywhere from infinite time to a millennium to mere fractions of a millisecond.
You can turn the “word list” function on or off as you test passwords. This tool works by cycling through a word list containing common words and passwords and then evaluating other factors such as character types. If you enter a password not on the word list, the cracking time will not be affected. But if your password is on the word list, it greatly affects cracking time.
Note: The interactive tool is for educational purposes only. Although it does not collect or store your passwords, you should avoid using your current password.
How long should your password be?
When it comes to passwords, one thing is certain: Size matters. Adding a single character to a password boosts its security exponentially. In a so-called “dictionary attack,” a password cracker will utilize a word list of common passwords to discern the right one. The list above shows the difference that adding characters can make when it comes to security.
For instance, if you have an extremely simple and common password that’s seven characters long (“abcdefg”), a pro could crack it in a fraction of a millisecond. Add just one more character (“abcdefgh”) and that time increases to five hours. Nine-character passwords take five days to break, 10-character words take four months, and 11-character passwords take 10 years. Make it up to 12 characters, and you’re looking at 200 years’ worth of security – not bad for one little letter.
alpha and numberic characters
Combining numbers and letters rather than sticking with one type of character dramatically enhances password security. A string of nine letters or numbers takes milliseconds to crack. Add a single letter, and your password may become cryptic enough to thwart password crackers for nearly four decades.
However, it’s not as simple as swapping your “e” for a “3” or adding a number at the end of a string of letters. Password attacking methods actually take advantage of those common habits. Your best bet is to simply make your password less predictable and more complicated.
asci, lowercase, and numeric characters
Combining several types of characters is an extremely effective way to make your password more cryptic. A simple, common word can be cracked in fractions of a millisecond. Inject a mix of lowercase and uppercase letters, numbers, and symbols (think @, %, and #), and your password can be secure for more than a decade.
password strength over time
Not every security issue comes down to password character types and length – time is also a major factor. Over the years, passwords weaken dramatically as technologies evolve and hackers become increasingly proficient. For example, a password that would take over three years to crack in 2000 takes just over a year to crack by 2004. Five years later, in 2009, the cracking time drops to four months. By 2016, the same password could be decoded in just over two months. This demonstrates the importance of changing passwords frequently.
what if you get hacked?
One morning, you open your email, and everything has gone haywire: Friends are chatting you to say they’ve received spam from your address. Your login history looks odd. You have a pile of bounce-back messages in your inbox and a bunch of strange messages in your sent box. You’ve been hacked – so what should you do?
First, recover your email account, and change your password (use our guidelines to formulate a strong one). Complete all the steps, such as changing security questions and setting up phone notifications. Because email is filled with personal information, you should also notify your bank, PayPal, online stores, and any other accounts to discern whether a breach has occurred. Be sure to change other passwords as well. Finally, notify your contacts in case emails sent from your account have compromised their information too. While not getting hacked at all is the best-case scenario, promptly taking these steps can make the best of a bad situation.
Protect yourself
As time goes on, it only becomes more likely that your password will be hacked – putting your most personal information at risk. By taking a few steps to enhance your password, you can exponentially minimize the risk of a breach. When it comes to passwords, size trumps all else – so choose one that’s at least 16 characters. And be sure to choose a mix of character types (numbers, uppercase and lowercase letters, and symbols) to further enhance its security.
What else can you do? Steer clear of words found in the dictionary, pronouns, usernames, and other predefined terms, as well as commonly used passwords – the top two in 2015 were “123456” and “password” (yes, you read that right). Also, never use the same password in different places (that forgotten account at a site you never use could lead to a bank account breach). Consider using a password generator in order to get a complex password with no discernible pattern to help thwart password crackers. Finally, if memorizing long strings of characters proves too taxing, consider adopting a password manager that stores all your passwords. No password is perfect, but taking these steps can go a long way toward security and peace of mind.
Methodology
10 Digit Numbers Wordlist
Using processor data collected from Intel and John the Ripper benchmarks, we calculated keys per second (number of password keys attempted per second in a brute-force attack) of typical personal computers from 1982 to today.
The results from our interactive feature may differ from those of other online password-testing tools due to factors such as different equations, processors, and word lists.
Our data are based on the following equations:
Number of possible character combinations:
(Password Type)^(Password Length)
Password Type is the number of possible characters.
Effective Cores:
1/((1-Efficiency Constant)+(Efficiency Constant/Processor Cores)) The Efficiency Constant we used is 0.99, and we assume that 99% of the processor’s operations can be dedicated to the password crack.
Processor GFLOPS:
10 Digit Numeric Wordlist Download
Processor Frequency * Effective Cores
Keys Per Second:
GFLOPS/Encryption Constant (gathered and calculated from John the Ripper benchmarks).
Time in seconds:
Seconds = Combinations/KeysPerSecond
Sources
Fair Use
Feel free to share the images and interactive found on this page freely. When doing so, please attribute the authors by providing a link back to this page and Better Buys, so your readers can learn more about this project and the related research.
|
Wordlist rules syntax.
Each wordlist rule consists of optional rule reject flags followed byone or more simple commands, listed all on one line and optionallyseparated with spaces. There's also a preprocessor, which generatesmultiple rules for a single source line. Below you will finddescriptions of the rule reject flags, the rule commands (many of themare compatible with those of Crack 5.0a), and the preprocessor syntax.
Rule reject flags.

Numeric constants and variables.
Numeric constants may be specified and variables referred to with thefollowing characters:
Sample Wordlist File Download
Here max_length is the maximum plaintext length supported for thecurrent hash type.
These may be used to specify character positions, substring lengths, andother numeric parameters to rule commands as appropriate for a givencommand. Character positions are numbered starting with 0. Thus, forexample, the initial value of 'm' (last character position) is one lessthan that of 'l' (length).
Character classes.
The complement of a class can be specified by uppercasing its name. Forexample, '?D' matches everything but digits.
10 Digit Numeric Wordlist List
Simple commands.
String commands.
To append a string, specify 'z' for the position. To prefix the wordwith a string, specify '0' for the position.
Although the use of the double-quote character is good for readability,you may use any other character not found in STR instead. This isparticularly useful when STR contains the double-quote character.There's no way to escape your quotation character of choice within astring (preventing it from ending the string and the command), but youmay achieve the same effect by specifying multiple commands one afteranother. For example, if you choose to use the forward slash as yourquotation character, yet it happens to be found in a string and youdon't want to reconsider your choice, you may write 'Az/yes/$/Az/no/',which will append the string 'yes/no'. Of course, it is simpler andmore efficient to use, say, 'Az,yes/no,' for the same effect.
Length control commands.
English grammar commands.
Insert/delete commands.
Also see the 'X' command (extract and insert substring) under 'Memoryaccess commands' below.
Note that square brackets ('[' and ']') are special characters to thepreprocessor: you should escape them with a backslash (') if usingthese commands.
Charset conversion commands.
Memory access commands.
If 'Q' or 'X' are used without a preceding 'M', they read from theinitial 'word'. In other words, you may assume an implied 'M' at thestart of each rule, and there's no need to ever start a rule with 'M'(that 'M' would be a no-op). The only reasonable use for 'M' is in themiddle of a rule, after some commands have possibly modified the word.
The intended use for the 'Q' command is to help avoid duplicatecandidate passwords that could result from multiple similar rules. Forexample, if you have the rule 'l' (lowercase) somewhere in your rulesetand you want to add the rule 'lr' (lowercase and reverse), you couldinstead write the latter as 'lMrQ' in order to avoid producing duplicatecandidate passwords for palindromes.
The 'X' command extracts a substring from memory (or from the initialword if 'M' was never used) starting at position N (in the memorized orinitial word) and going for up to M characters. It inserts thesubstring into the current word at position I. The target position maybe 'z' for appending the substring, '0' for prefixing the word with it,or it may be any other valid numeric constant or variable. Some exampleuses, assuming that we're at the start of a rule or after an 'M', wouldbe 'X011' (duplicate the first character), 'Xm1z' (duplicate the lastcharacter), 'dX0zz' (triplicate the word), '<4X011X113X215' (duplicateevery character in a short word), '>9x5zX05z' (rotate long words left by5 characters, same as '>9{{{{{'), '>9vam4Xa50'l' (rotate right by 5characters, same as '>9}}}}}').
Numeric commands.
'l' is set to the current word's length, and its new value is usable bythis same command (if N or/and M is also 'l').
V must be one of 'a' through 'k'. N and M may be any valid numericconstants or initialized variables. It is OK to refer to the samevariable in the same command more than once, even three times. Forexample, 'va00' and 'vaaa' will both set the variable 'a' to zero (butthe latter will require 'a' to have been previously initialized),whereas 'vil2' will set the variable 'i' to the current word's lengthminus 2. If 'i' is then used as a character position before the word ismodified further, it will refer to the second character from the end.It is OK for intermediate variable values to become negative, but suchvalues should not be directly used as positions or lengths. Forexample, if we follow our 'vil2' somewhere later in the same rule with'vj02vjij', we'll set 'j' to 'i' plus 2, or to the word's length as ofthe time of processing of the 'vil2' command earlier in the rule.
Character class commands.
Extra 'single crack' mode commands.
When defining 'single crack' mode rules, extra commands are availablefor word pairs support, to control if other commands are applied to thefirst, the second, or to both words:
If you use some of the above commands in a rule, it will only processword pairs (e.g., full names from the GECOS field) and reject singlewords. A '+' is assumed at the end of any rule that uses some of thesecommands, unless you specify it manually. For example, '1l2u' willconvert the first word to lowercase, the second one to uppercase, anduse the concatenation of both. The use for a '+' might be to apply somemore commands: '1l2u+r' will reverse the concatenation of both words,after applying some commands to them separately.
10 Digit Numeric Wordlist Word
The rule preprocessor.
The preprocessor is used to combine similar rules into one source line.For example, if you need to make John try lowercased words with digitsappended, you could write a rule for each digit, 10 rules total. Nowimagine appending two-digit numbers - the configuration file would getlarge and ugly.
10 Digit Numeric Wordlist Free
With the preprocessor you can do these things easier. Simply write onesource line containing the common part of these rules followed by thelist of characters you would have put into separate rules, in squarebrackets (the way you would do in a regexp). The preprocessor will thengenerate the rules for you (at John startup for syntax checking, andonce again while cracking, but never keeping all of the expanded rulesin memory). For the examples above, the source lines will be 'l$[0-9]'(lowercase and append a digit) and 'l$[0-9]$[0-9]' (lowercase and appendtwo digits). These source lines will be expanded to 10 and 100 rules,respectively. By the way, preprocessor commands are processedright-to-left while character lists are processed left-to-right, whichresults in natural ordering of numbers in the above examples and inother typical cases. Note that arbitrary combinations of characterranges and character lists are valid. For example, '[aeiou]' will usevowels, whereas '[aeiou0-9]' will use vowels and digits. If you need tohave John try vowels followed by all other letters, you can use'[aeioua-z]' - the preprocessor is smart enough not to produce duplicaterules in such cases (although this behavior may be disabled with the'r' magic escape sequence described below).
There are some special characters in rules ('[' starts a preprocessorcharacter list, '-' marks a range inside the list, etc.) You shouldprefix them with a backslash (') if you want to put them inside a rulewithout using their special meaning. Of course, the same applies to 'itself. Also, if you need to start a preprocessor character list at thevery beginning of a line, you'll have to prefix it with a ':' (the no-oprule command), or it would be treated as a new section start.
Finally, the preprocessor supports some magic escape sequences. Thesestart with a backslash and use characters that you would not normallyneed to escape. In the following paragraph describing the escapes, theword 'range' refers to a single instance of a mix of character listsand/or ranges placed in square brackets as illustrated above.
Currently supported are '1' through '9' for back-references to priorranges (these will be substituted by the same character that iscurrently substituted for the referenced range, with ranges numberedfrom 1, left-to-right), '0' for back-reference to the immediatelypreceding range, 'p' before a range to have that range processed 'inparallel' with all preceding ranges, 'p1' through 'p9' to have therange processed 'in parallel' with the specific referenced range, 'p0'to have the range processed 'in parallel' with the immediately precedingrange, and 'r' to allow the range to produce repeated characters. The'r' escape is only useful if the range is 'parallel' to another one orif there's at least one other range 'parallel' to this one, because youshould not want to actually produce duplicate rules.
Please refer to the default configuration file for John the Ripper formany example uses of the features described in here.
$Owl: Owl/packages/john/john/doc/RULES,v 1.14 2017/05/14 12:16:07 solar Exp $